Julia Wolińska
The top corporations agree about our predictions concerning the future. Every year we hear more and more promises about the Internet of Things, which is going to make us forget about all our issues... even if we did not know about their existence!
After leaving the work you are going to get into your car, which is going to bring you right to the address of your home. With only a single touch you can turn on the lights and check if the current contents of your fridge can satisfy your cravings. Just remember not to drink your coffee – your health monitoring app will make sure that you don’t succumb to unhealthy habits and it already knows your blood pressure should not be too high! It is just hard to believe that the internet alone can make your life so much more convenient
However, the moment you lay down on your comfy sofa, something else happens. During the synchronisation of data from your virtual debit card and your navigation app, you are not the only one gaining the info from them. Your actions are actively being watched by hackers. They are making sure that they know your address and the time you are leaving your house.
While it can really sound like a vision from some science fiction thriller, it’s entirely possible that the incoming technological revolution will lead to such circumstances. The question appears; would we surrender our privacy for an access to incredible convenience?
You could, however, also protecting your data. Then you would not have to expose yourself to potential data theft and use all of the miracles of technology without a single worry. How, you my ask? The answer lies in the block of chains.
Vulnerable data and its risks
Take a moment to consider how does the information flow within your family and friend groups. Well, naturally, it is usually done by verbal exchanges which usually letyou know about their customs, preferences and habits. During conversations, you and your friends gather data about each other, you learn about the music you listen to, what do you want to eat for dinner or if you are allergic to peanuts.
As it turns out, the domestic appliance or even car manufacturers wish to initiate the same dialogue with you - they want to get to know you as well as your friends and family do through the power of internet. They are aiming to adapt their appliances to improve your experience with them and they want to do that by gathering the necessary data about your everyday life.
However, the problem arises the moment we are talking about the vulnerable data. It is for example your address, information about your bank accounts or investments, your workplace or data about your customers, details about your health. This is the data that should not ever be revealed to any unwanted third parties but are often unfortunately under the attack from hackers.
It turns out that if your everyday use devices are connected to the internet, it is possible to hack not only your computer or your laptop but also your domestic appliances and car.
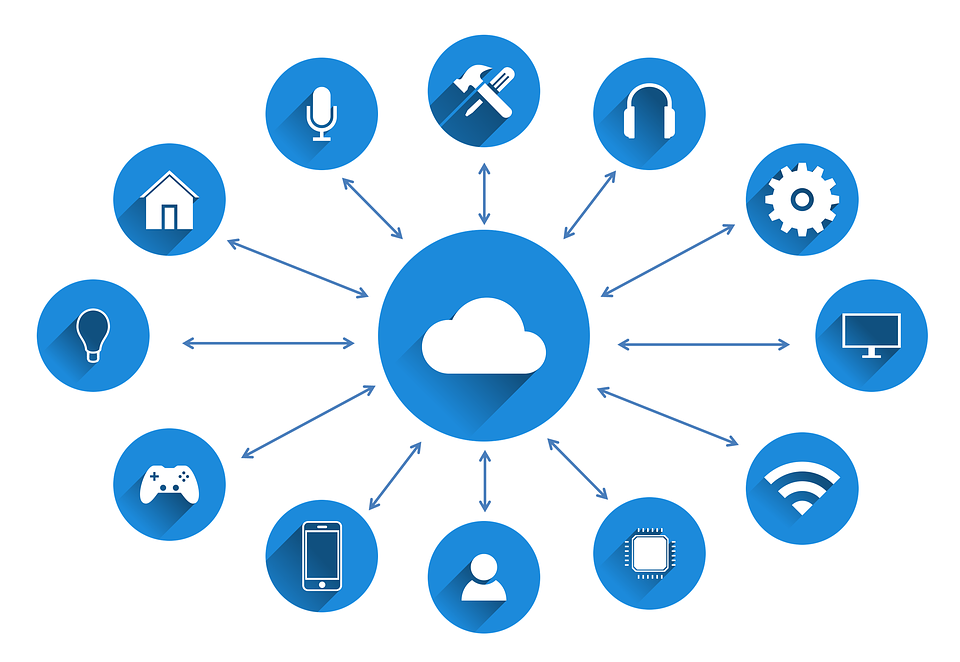
More often do the voices appear that the internet in its modern form is not a good foundation for the absolutely humongous network of the internet of things. That is why the research has begun to find a safer, more anonymous medium which would not be as vulnerable towards the attacks. The experts believe that no other technology than the one offered by the blockchain would suffice to pull this task off.
Blockchain - the way to keep the IoT safe
Blockchain was made viral during the time of the cryptocurrency boom in 2016. However, there is still a lot of people who find the concept quite enigmatic. It is often wrongly associated with the phenomenon of Bitcoins. After all, the usability of the blockchain goes far beyond the financial sector. We can briefly say that it is a kind of technology which is used to gather the data about our transactions on the internet safely and anonymously.
Blockchain is a database which is formed by the chain of the blocks connected to it, which it derives its name from. Each and every individual block is connected to next one. What’s important is that all the gathered and saved information are not stored onone server or on one device – they are scattered and encrypted and their anonymouscopies are held inside of multiple locations. Thanks to this method the risk of hacking or stealing such data is equal to zero.
The public registry can be presented as a giant piece of paper which holds every single data concerning your address, financial data or even health which was copied and sent to multiple locations around the world. Those pieces of paper are interconnected in a cryptographic way. They are constantly compared and “prescribed” on new datasheets. That means that the mathematic properties can assure that they cannot be removed, replaced or completely altered.
The mechanism does not only help us fight against the scams, but also allows us to learn about the external conditions such as the weather, which can be also verified by the use of the modern systems.
Chained data- how to keep it safe
According to the most recent report „IoT in Poland”, 47% of Poles are afraid that theirdata can be leaked and 33% of them are afraid of losing the control over their devices connected to the web. Will those anxieties be fixed by the blockchain? Perhaps this might be the foundation for the new network to which most of the modern devices will be connected to with the usage of IoT. Its almost impossible to hack the block of chains because of its complexity, while hacking the home WiFi only requires a moderate IT knowledge.
Currently, if we forget to turn off the sink, the only risk we create is potentially floodingour neighbours’ flat. However, if we forget about the safe usage of IoT devices, we are can potentially face much greater consequences like the risk of hacking the entirenetwork they are connected to. Without the blockchain we will be potentially risking not only the safety of our data, but also the data belonging to our clients. When will the ideal, safe and practical future unfold? No one can truly tell, but we must remain vigilant and teach the companies to slowly but steadily implement the blockchain technology.
 en
en  pl
pl