Blockchain technology, artificial intelligence (AI), and cryptocurrencies have transformed how digital transactions and value exchanges occur. It is crucial to ensure the security of digital assets as businesses and individuals adopt these technologies. One vital aspect of protecting digital assets is employing multi-signature wallets.
In this developer's guide, we will dive deep into multi-signature wallets, equipping you with the knowledge and insights needed for successful implementation. For blockchain developers, cryptocurrency exchange platforms, or companies handling high-value transactions, understanding multi-signature wallets is vital to improve security and reduce the risks associated with single-key wallets.
This guide will discuss the definition and concept of multi-signature wallets, their advantages and use cases, and examine the key elements that contribute to their security and robustness. We will also offer a step-by-step breakdown of the implementation process, including wallet generation, transaction creation and signing, as well as wallet recovery and key management.
Additionally, we will tackle common challenges developers face when implementing multi-signature wallets and provide best practices for overcoming these obstacles. By the conclusion of this guide, you will possess a thorough understanding of multi-signature wallets and have the essential knowledge to incorporate them into your blockchain-based applications or systems.
Understanding Multi-Signature Wallets
Explanation and Principle
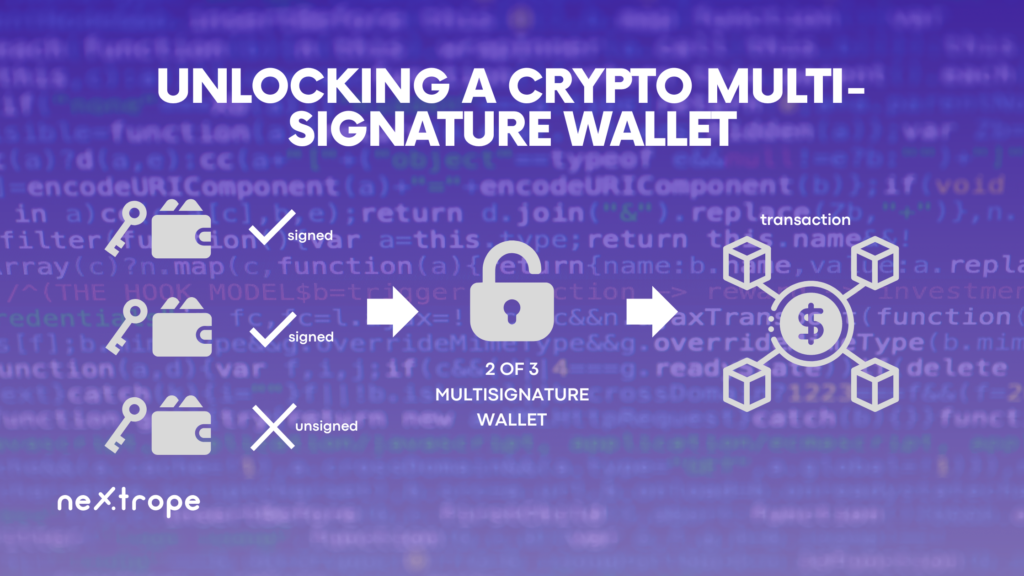
Within the realm of cryptocurrencies, a multi-signature wallet, commonly referred to as a multisig wallet, is a digital wallet variety that mandates multiple signatures for transaction authorization. In contrast to conventional single-key wallets that depend on one private key for approving transactions, multi-signature wallets allocate signing authority among several participants.
The core idea of multi-signature wallets focuses on enhancing security while minimizing the chances of unauthorized access or fraudulent transactions. By necessitating multiple signatures, these wallets add an extra layer of defense, making it harder for ill-intentioned actors to breach the wallet and pilfer digital assets.
Check out the list of 12 Multi-sig wallets
Benefits and Applications
- Security Enhancement
Comparing with single-key wallets, multi-signature wallets notably improve security levels. Requiring multiple signatures makes it difficult for an intruder to seize the wallet's control and carry out unauthorized transactions. The wallet remains protected even if one key is compromised as more signatures are necessary.
- Organizational Settings
Corporate settings greatly benefit from multi-signature wallets when multiple stakeholders' approvals are needed for financial procedures. Employing such a wallet enables organizations to guarantee that no lone individual exercises full control over the company's funds, thus diminishing the possibility of internal fraud.
- Cryptocurrency Exchanges and High-Value Transactions
Handling considerable quantities of digital assets, cryptocurrency exchanges become appealing targets for cybercriminals. By adopting multi-signature wallets, these exchanges can implement rigorous security protocols, mandating multiple authorizations for withdrawals and reducing unauthorized asset transfer risks.
- Escrow Functions
Multi-signature wallets frequently serve in escrow functions, where a neutral third party retains funds during a transaction until specified conditions have been met. The presence of multiple signatures assures that every party in the transaction provides consent before releasing the funds.
- Jointly Managed Accounts
In scenarios where numerous individuals or entities jointly manage a digital asset wallet, such as business collaborations or familial accounts, multi-signature wallets guarantee collective transaction decision-making, mitigating the chances of unilateral actions and fostering trust among members.
By understanding multi-signature wallets' benefits and applications, one can lay the groundwork for utilizing their potential in fortifying digital asset security. In the following section, we will delve into multi-signature wallets' fundamental components, offering insights into their functioning and contribution to the overall security structure.
Essential Elements of Multi-Signature Wallets
Several vital elements make up a multi-signature wallet, working collectively to maintain its security and functionality. For developers who aim to effectively implement multi-signature wallet solutions, grasping these essential components is critical. Let's examine these elements more closely:
Public and Private Keys
- Public Keys
Generated from their corresponding private keys, public keys are cryptographic addresses that function as unique identifiers for receiving funds in a multi-signature wallet. These public keys can be shared freely and utilized by anyone to confirm the legitimacy of transactions linked with the wallet.
- Private Keys
Private keys are confidential, randomly created cryptographic codes that allow access to the funds held within a multi-signature wallet. Each participant in such a wallet owns a private key which must be securely stored and not shared with unauthorized parties to prevent unwarranted access to the wallet.
Signature Threshold
- Signature Requirement
The signature threshold refers to the minimum number of signatures needed to approve a transaction from a multi-signature wallet. This determines the security level and control over the wallet. A 2-of-3 signature threshold, for instance, would necessitate two out of three authorized participants' approval for a transaction.
- Flexibility and Security
Selecting an appropriate signature threshold depends on finding the right balance between flexibility and security. A higher threshold ensures increased security through requiring more signatures but might create difficulties regarding transaction speed and convenience. In contrast, a lower threshold offers more flexibility but could jeopardize security.
Address Types
- Pay-to-Script-Hash (P2SH)
P2SH is a commonly used address type for multi-signature wallets, enabling the creation of a redeem script that defines the conditions necessary for spending funds. The redeem script comprises authorized participants' public keys and the signature threshold.
- Pay-to-Witness-Script-Hash (P2WSH)
Introduced alongside the Segregated Witness (SegWit) upgrade, P2WSH is an address type that offers enhanced security and decreased transaction size. P2WSH addresses place the redeem script within the transaction's witness section, improving the scalability and efficiency of multi-signature transactions.
Comprehending the roles and functionalities of these crucial components is fundamental for successfully implementing multi-signature wallets. In the subsequent section, we will explore the implementation process of multi-signature wallets in-depth, equipping developers with a comprehensive guide to effectively generate, transact, and manage these wallets.
Implementing Multi-Signature Wallets
For the successful implementation of multi-signature wallets, it is crucial to follow secure principles and pay close attention to detail. In this part, we present a comprehensive guide to aid developers in incorporating multi-signature wallets seamlessly into their applications or systems.
Generating Wallets
- Establish Signature Threshold
Select the optimal signature threshold based on your multi-signature wallet's security needs and flexibility.
- Produce Public/Private Key Pairs
Using cryptographic libraries or tools, produce a unique public/private key pair for every individual involved in the multi-signature wallet. Guarantee that the keys are safely generated and stored, adhering to key management best practices.
- Construct Multi-Signature Address
Employ suitable libraries or tools to construct a multi-signature address, like a P2SH or P2WSH address. Define the necessary number of signatures and input the authorized participants' public keys.
Creating and Signing Transactions
- Identify Transaction Inputs and Outputs
Determine the transaction inputs (funds being used) and outputs (target addresses) for the intended transaction from the multi-signature wallet.
- Assemble Transaction
Construct the transaction using the transaction details and the multi-signature address as input. Make sure that the transaction complies with your chosen blockchain platform's rules and protocols.
- Authorize Transaction
All authorized members must employ their private keys to authorize the transaction. Merge the signatures as needed by the signature threshold.
Recovery of Wallets and Key Management
- Backup and Safekeeping of Keys
Securely backup and keep all private keys related to the multi-signature wallet. Utilize secure storage solutions like hardware wallets, encrypted digital storage, or offline backups.
- Rotation of Keys
To improve security, think about employing key rotation strategies periodically. Generate new key pairs and modify the multi-signature wallet setup accordingly. Manage the shift to new keys carefully to prevent any interference with wallet operations.
- Establishing Recovery Procedures
Develop a recovery plan for situations where keys are lost or compromised. Lay out the actions and protocols for retrieving funds from the multi-signature wallet, which includes verifying participants' identities and initiating the necessary key replacement or regeneration.
Adhering to these implementation guidelines enables developers to effectively integrate multi-signature wallets into their blockchain-based applications or systems. It is essential to recognize that challenges might present themselves during implementation. In the following section, we will explore common obstacles and offer best practices for developers working with multi-signature wallets.
Common Challenges and Best Practices
Implementing multi-signature wallets can present certain challenges for developers. In this section, we will explore some common challenges and provide best practices to overcome them effectively.
Common Challenges
- Compatibility with Existing Wallets and Services
Integrating multi-signature wallets with existing wallets or services may pose compatibility challenges. Ensure compatibility by verifying the supported address types and transaction formats of the wallets and services involved.
- Key Management
Managing and securely storing private keys can be complex, especially when multiple participants are involved. Implement robust key management practices, such as encryption, hardware wallets, or distributed key management systems, to safeguard the private keys.
- User Experience
Multi-signature transactions require additional steps and coordination between participants, which can impact user experience. Streamline the user interface and provide clear instructions to ensure a smooth and intuitive experience for users interacting with the multi-signature wallet.
Best Practices
- Security Measures
Implement rigorous security measures throughout the entire development and deployment process. This includes secure key generation, encryption, secure storage of keys, secure communication channels, and comprehensive testing for vulnerabilities.
- Code Reviews and Audits
Conduct regular code reviews and security audits to identify and address potential vulnerabilities and weaknesses in the implementation of the multi-signature wallet. Engage external security experts to perform thorough audits for an unbiased evaluation.
- Thorough Testing
Perform extensive testing of the multi-signature wallet implementation, including unit tests, integration tests, and end-to-end tests. Test various scenarios and edge cases to ensure the reliability and robustness of the wallet.
Documentation and Education:
Provide clear and comprehensive documentation for developers and users on how to interact with the multi-signature wallet. Educate users about the benefits and security features of multi-signature wallets to build trust and encourage adoption.
- Regulatory Compliance
Consider regulatory requirements and compliance standards applicable to your jurisdiction when implementing multi-signature wallets. Ensure adherence to relevant regulations, such as Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements.
By adhering to these best practices, developers can mitigate risks, enhance security, and improve the overall functionality and user experience of multi-signature wallets.
Read also our guide - Building Decentralized Oracles
Conclusion
Multi-signature wallets boost security and management of digital assets by necessitating multiple authorizing signatures for transactions. In this guide, we delved into the meaning, merits, and essential aspects of multi-signature wallets. A comprehensive implementation tutorial was presented for developers, encompassing wallet creation, transaction generation and signing, along with wallet restoration and key administration.
Implementation of multi-signature wallets can pose challenges; however, adhering to best practices such as stringent security protocols, code examinations, exhaustive testing, and ample documentation can aid in surmounting these hurdles. By employing multi-signature wallets, both businesses and individuals can safeguard their digital holdings, especially in corporate settings, exchanges, high-value deals, escrow provisions, and shared accounts.
As blockchain technology advances and influences diverse sectors, prioritizing digital asset safety and integrity is imperative. Adopting multi-signature wallets plays a pivotal role in accomplishing this aim. By grasping the notions and best practices detailed in this guide, developers are well-equipped to incorporate multi-signature wallets into their software applications, fortifying security and guaranteeing the reliability of transactions in the virtual space.
Do you need help with Implementing Multi-Signature Wallets? Or maybe you look for exceptional Web3 & Blockchain developers for your project? Contact us!
 en
en  pl
pl